What's New - March 2012
[Home]
March 6, 2012: "If you draw a 9x9 by nine grid, thus giving yourself 81 small squares; how many rectangles can you count in total? " An little 20 line program, Rectangle Counts, finds the answer and also leads to some interesting math.
March 12, 2012:
|
|
|
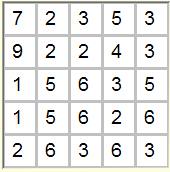
Typical solution using digits 1,1,2,2,2,2,2,3,3,3,3,3,3,4,5,5,5,5,6,6,6,6,6,7,9 |
A solver for a "Special" 5x5 Magic Square was posted today. I call it "Special" because we are given a specific set of 25 integers from 1 to 9 (with repeats), which must be used to fill the square. The typical 5x5 Magic Square contains integers from 1 to 25 with rows, columns, and diaginals summing to 65. Each row, column and diagonal in this case must sum to 20.
A good exercise in Combinatorics and pruning search spaces!
The final version finds about 5 solutions per second for the
first 5000.
March 19, 2012: I had some fun and learned some things this week writing a Squared Palindromes program which investigates finding the smallest "even" palindrome which is the square of another integer.
March 21, 2012: A small update was posted today to clean up some documentation errors in the description screens of our RSA Keys Demo program. RSA stands for the last names of the 3 guys that published an algorithm allowing secure message exchange. In simplest terms, RSA encryption works like this:
|
|
A wants to be able to receive secure messages from B. |
|
|
Alice has a key with public and private parts generated using some well known mathematical magic using random numbers. She publishes or sends the public part of the key to Bob. (A and B are always Alice and Bob. J) |
|
|
B can encrypt his message using A's public key, using some more agreed upon (and public) math magic. |
|
|
B sends the encrypted message to A (and inadvertently to any eavesdroppers). |
|
|
Using a third bit of math magic which includes her private key, A decrypts B's message and accepts his offer to dinner. |
|
|
The eavesdroppers having A's public key, the encrypted message, and all of the math magic techniques still cannot find out when and where the dinner will take place because they do not know A's private key. |
Interesting stuff!